WordPress Security and Hacks
Recently the DACS website was “hacked”. A rogue script was inserted into the header of the pages.
Several steps were taken to sanitize the WordPress installation and this fixed the problem – temporarily. However, security is an ongoing battle, and new threats and hacks appear all the time.
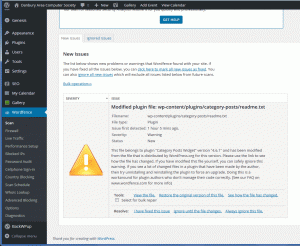
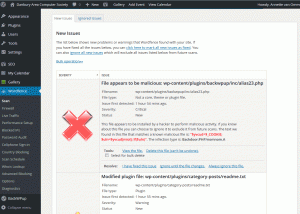
The security breach was detected by the WordFence plugin. An automated email was sent to the webmasters indicating which files were compromised.
Below are steps I took to fix the problem temporarily:
- I logged into the DACS site and opened up the Wordfence/Scan page. The offending pages were listed. WordFence offers several options to deal with these. The “file type” will determine what to do. Delete? Repair? Ignore? Look carefully at the options. (This screen shot is not of the same incidence so only serves as an example.)
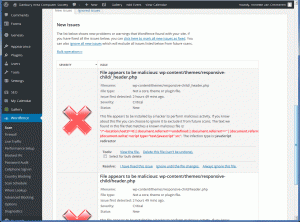
- In the DACS case, several theme files, and several core files were affected.
- I let WordFence delete or repair everything, but that did not solve the problem. The script could be seen in the source code of the page, in the head section.
- To be safe I went to Dashboad/Updates and “reinstalled” WordPress. Hopefully that took care of the core files, although WordFence had already deleted the offending files.
- Next I figured the theme needs to be fixed. The DACS site uses a Child Theme of Genesis. The Child theme does NOT have a header.php file, but the parent theme Genesis does. I downloaded a new copy of the Genesis theme, and uploaded it via FTP, overwriting the old theme files.
- This got rid of the script. However, it’s only a temporary fix, as a day later another header.php file, from an inactive theme was affected.
- This tells me there has to be a ‘back door’ file somewhere that’s creating these script inserts. (See below)
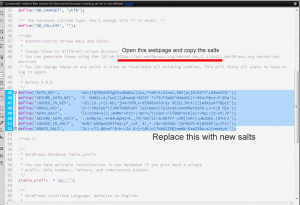
- I also reset the “salts”. These are found in the wp-config.php file. This deletes all user cookies and forces everyone to login again. Recommended is for everyone to change passwords.
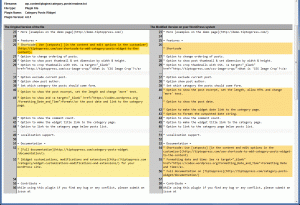
Sample of a changed file warning in Wordfence:
Look at the result of the “changes” screen. Is this a threat or is this ‘ok’?
Several folders that were added to the root of the server on Bluehost. How did they get there? Account password to Bluehost was reset, hopefully preventing any more intrusions.